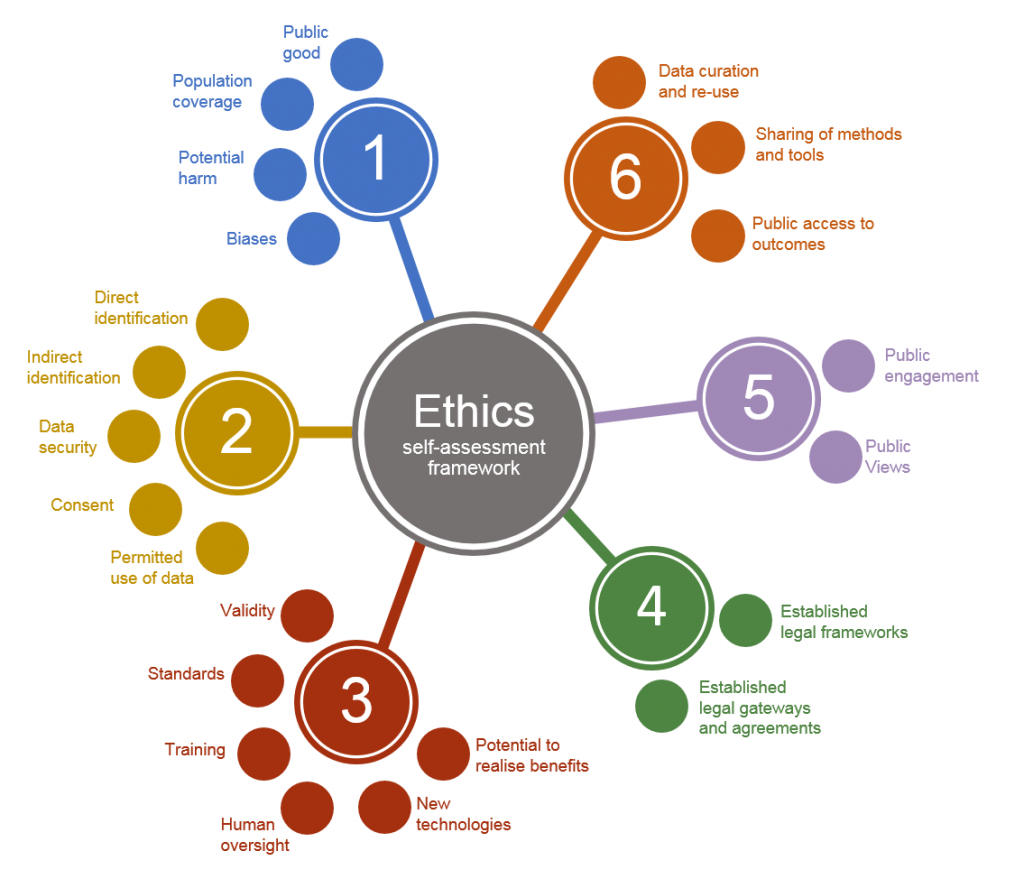
The ethics self-assessment process aims to offer researchers an easy-to-use framework to review the ethics of their projects throughout the research cycle. The self-assessment provides a timely means to identify ethical issues and shape future discussions. The process aims to support an accurate and consistent estimation of the “ethical risks” of research proposals.
The self-assessment form and guidance can be found in the ‘Self-assessment Tool and Guidance’ section on the right. The Data Ethics team can support you when completing the self-assessment by offering further guidance, advice and training. Please contact us, at Data.Ethics@statistics.gov.uk.
Following a period of engagement and consultation with analysts across the research community, a revised version of the ethics self-assessment tool was launched on 31 March 2022. For analysts that are currently using previous iterations of the self-assessment tool, guidance to support the use of such versions is available via an archive link below.
This guidance is only intended for use by those who are using previous iterations of the self-assessment tool, before it was updated on 31 March 2022.
Self-Assessment Guidance v2.3 [pdf 478 KB]
